SOLUTION
Delegated Authorization
Principled delegation Per‑action constraints Auditable access
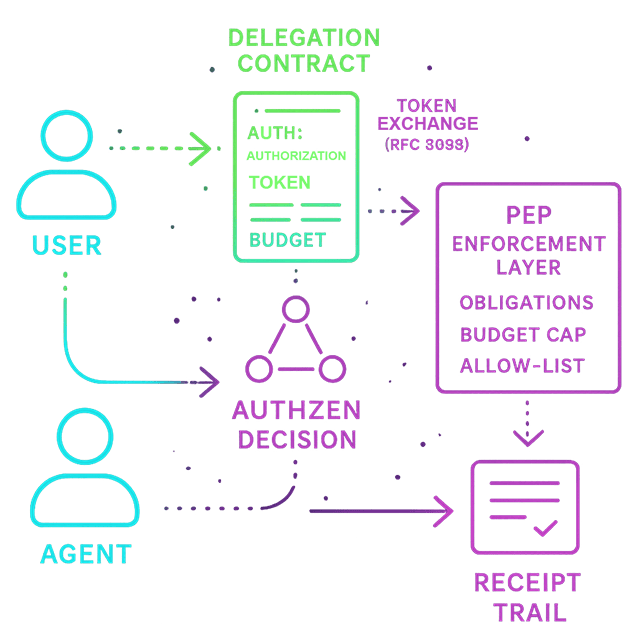
How it works
Membership models orgs, teams, roles, and delegations. PDP evaluates each request with these relationships and policy to return decisions.
Standards
- OpenID AuthZEN decisions with obligations/TTL
- Token Exchange (RFC 8693) for on‑behalf‑of
- SCIM for membership synchronization