OpenID AuthZEN–compliant PDP
Interoperable JSON decisions for gateways and services. EmpowerNow extensions add constraints, obligations, and TTL.
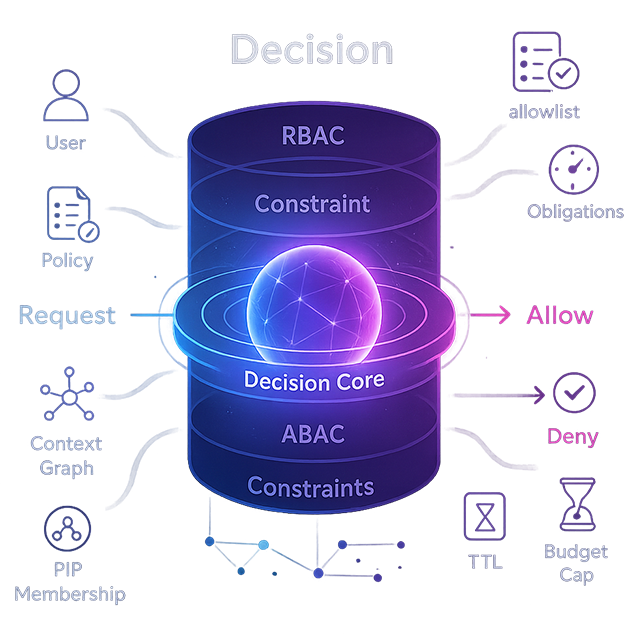
Why it wins
How it works
Subject/Resource/Action/Context → PDP → Decision. PEPs enforce constraints (sync) and obligations (async). Batch multiple checks in one call for faster pages and smoother agent runs. Deploy once to gateways/services; adopt incrementally via a PDP facade and PEP middleware.
What it is
A standards‑credible authorization brain that evaluates ABAC + relationships and returns AuthZEN‑style decisions. EmpowerNow decision extensions add constraints (sync guardrails) and obligations (async actions) so gateways and services can enforce consistently.
What you get
- Cost control for AI agents: stop runaway spend (HTTP 402), cap tokens, restrict models/egress
- Fewer bespoke integrations: one JSON decision contract across PEPs and vendors
- Faster delegated flows: model human↔human and human↔agent delegations once; reuse everywhere
- Audit confidence: signed, hash‑chained receipts and human‑readable reasons
Why it's unique
- Graph‑anchored ABAC: policy logic in YAML via Policy nodes; fast‑moving edge constraints (budget, trust, expiry) live in graph
- Hybrid ReBAC + ABAC: delegations, teams, ownership from the Membership Service (Neo4j) without role explosion
- Delegation kits: human↔human and human↔agent OBO with spend caps, trust levels, expiry, consent
- AuthZEN interop: decision exchange aligned to the OpenID WG; extensions (constraints/obligations/TTL) are product‑level
- Plan/schema pinning: deny off‑plan tool calls and catch schema drift pre‑exec (MCP Gateway)
- Proof by receipts: signed, hash‑chained receipts for audit and chargeback
See it
Send multiple checks in one call for faster pages and smoother agent runs.
AuthZEN compliance
Compatible with AuthZEN decision exchange across PDP/PEP/PIP/PAP. We keep ABAC; you adopt interoperable JSON. EmpowerNow adds decision extensions (constraints, obligations, TTL) for practical enforcement.
Note: Extensions are product‑level and not part of the current AuthZEN spec.
AI Agent governance
- Budget holds and settle; HTTP 402 upgrade CTA
- Model routing to mini; streaming token caps
- Egress/model allow‑lists; consent obligations at issuance
Decision example (EmpowerNow extensions)
{
"decision": "Permit",
"ttl": 3000,
"constraints": {
"models_allow": ["gpt-4o-mini"],
"egress_allow": ["*.example.com"],
"stream_tokens_max": 2048
},
"obligations": [
{ "type": "budget_hold", "limit_usd": 2.00, "call_id": "abc-123" }
],
"reasons": ["policy:agent.tools.invoke"]
}
Hybrid ReBAC with Membership Service
Combine ABAC attributes with relationship edges (delegations, teams, ownership) from the Neo4j‑backed Membership Service PIP for dynamic, auditable access.
Relationship data shape
{
"relationships": [
{ "type": "member_of_team", "subject": "user_123", "object": "team_finance" },
{ "type": "delegates_to", "subject": "manager_9", "object": "user_123", "capabilities": ["approve"], "status": "active" }
]
}
Proof
- Explainable decisions with reasons; every action emits a signed receipt
- Budget/content/params enforced via constraints and obligations
- Integrates with Membership Service (ReBAC) and Inventory/Search as PIPs
Integrations
Works with your gateways, LLM providers, and data plane.
Is this for me?
- Platform teams: standardize decisions across gateways and services
- Security architects: budgets/egress/models; explainability + receipts
- App teams: one middleware; fewer roles via delegations and ownership
Compatible with AuthZEN decision exchange; EmpowerNow decision extensions (constraints, obligations, TTL) enable practical enforcement.
AI chat budget 402
Safe stop + upgrade CTA.
Off‑plan tool deny
Plan step mismatch.
Plans
Read more
What's next?
Learn more
Technical docs
Marketing site
Related reading
Compare
- OPA/Cerbos: no standard AuthZEN envelope (constraints/obligations/TTL) or conservative merge → evidence
- AWS AVP: managed PDP; Cedar allow/forbid model without AuthZEN response semantics → evidence
- Envoy/Istio: excellent PEPs; decision contract depends on the PDP; AuthZEN provides explainability + obligations → evidence