ARIA SHIELD
ARIA Shield
Enforce budgets & streaming caps at runtime—zero-token SPA.
Enterprise SaaSRegulated +1 more
Why it wins
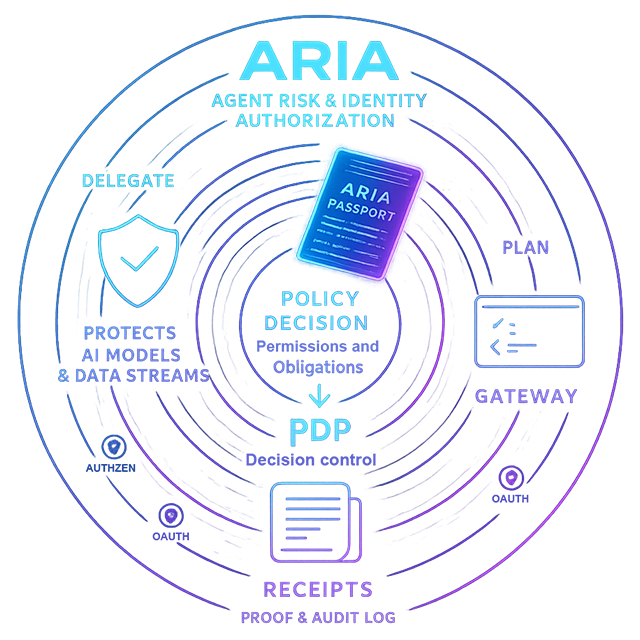
How it works
- Edge authenticates SPA with HTTP-only cookies, not tokens.
- BFF validates session and requests PDP decision per route.
- On allow, BFF brokers per-service tokens and applies constraints.
- Receipts are signed and chained; budgets settle to actuals.
Budget semantics (HTTP 402)
HTTP/1.1 402 Payment Required
Content-Type: application/json
{
"error": "budget_exceeded",
"call_id": "abc-123",
"policy": "llm.invoke",
"remaining_usd": 0.00,
"retry_after_s": 86400
}
When a route exceeds its budget, Shield returns a deterministic 402 with call_id and remaining budget. On permit, the hold is settled to actuals and linked in the receipt.
Streaming caps
// Pseudocode
const caps = { tokensMax: 2048, durationMsMax: 20000 };
shield.stream(model, request, caps, onChunk);
Streaming stops early when token or duration limits are reached as dictated by PDP constraints.
Plans
Trusted by
Videos
The Unlikely Hero of AI Security
Onboarding Your AI
Ready to see streaming caps and receipts?
Watch the 10-minute tour or talk to us for a deep dive.