What is ARIA? — Agent Risk & Identity Authorization
ARIA is our AI governance initiative: Shield (AI Model PEP) + MCP Gateway (tool PEP) with a PDP that returns constraints/obligations and a Receipt Vault for provable audit.
- Budget caps (402)
- Egress control
- Cryptographic receipts
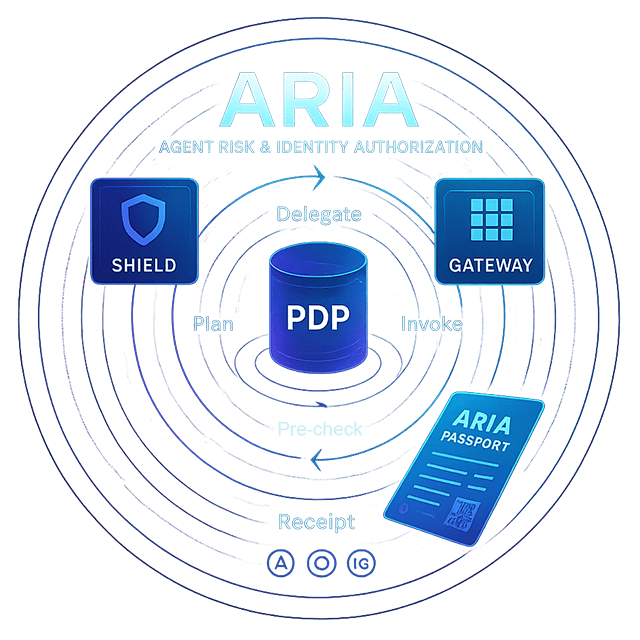
ARIA at a glance
ARIA (Agent Risk & Identity Authorization) provides provable guardrails for AI: create governed tools, enforce policy at the edge, and prove every action with receipts.
ARIA Shield
Policy Enforcement Point for LLM traffic: sessions not tokens; budgets, egress, and stream‑time truncation.
Learn Shield →MCP Gateway
Policy Enforcement Point for tools: schema pins, plan steps, allow‑lists, signed receipts.
Learn Gateway →How ARIA works
Flow at a glance
- Delegate: Alice delegates a Travel Agent with scope (budget, tools) recorded in Membership (Neo4j PIP).
- Plan: The agent plans an itinerary via the LLM. The call goes through ARIA Shield (PEP‑1).
Shield classifies the prompt and attaches attributes (models, egress domain, purpose).
- Pre‑check: Shield asks the PDP for a decision with context (delegator ↔ agent, classification).
PDP reads delegation constraints from the PIP (Membership graph).
- Tool: The agent executes a tool (book flight) via ARIA MCP Gateway (PEP‑2).
Gateway validates schema pins/plan steps before the model or tool runs.
- Decision: PDP returns Permit with constraints (egress_allow, models_allow, spend_budget) and obligations (audit_log, receipt_emit, run_workflow) plus a TTL.
- Enforce: PEPs enforce in real time — Shield applies budget/egress/model caps; Gateway enforces schema and plan discipline.
- Prove: Both PEPs emit signed receipts. Analytics update spend and remaining budgets.
Actors & boundaries
| Actor | Role | Boundary |
|---|---|---|
| Alice | Delegator | Grants scope in Membership (PIP) |
| Travel Agent | AI Agent | Uses tools under delegation |
| ARIA Shield | PEP‑1 | LLM gateway: classify, cap, egress |
| ARIA MCP Gateway | PEP‑2 | Tool gateway: schema/plan discipline |
| PDP | Decision | Returns constraints + obligations |
What the PDP returns
- Decision: Permit/Deny with TTL for re‑use.
- Constraints: egress_allow, models_allow, spend_budget, data_scope.
- Obligations: audit_log, receipt_emit, run_workflow, consent.
Decisions with constraints and obligations
The PDP returns constraints the PEP enforces synchronously (egress_allow, models_allow, data_scope, spend_budget) and obligations the PEP performs after (audit_log, run_workflow, consent). This turns policy into precise, real‑time control.
ARIA for AI Delegation
Safer agent delegation without rewrites: you approve, we apply guardrails, and every action leaves a receipt.
- Delegate with guardrails — scope, time, location, budget
- One identity model — people, services, and agents governed the same way
- Explainable decisions — clear reasons, not just allow/deny
Threats → Controls
| Threat | Control | Enforced by |
|---|---|---|
| Schema drift | Schema pins (version/hash, grace window) | MCP Gateway |
| Overspend | Pre‑gate budgets + stream‑time settle | PDP + Shield |
| Prompt leakage | Egress allow‑lists, classification policies | Shield |
| Replay/token theft | Pairwise sub, act.sub, optional DPoP | IdP + PEPs |
| Missing audit | Signed, hash‑chained receipts | PEPs + Receipt Vault |
How it works (end‑to‑end)
- Ingress with ARIA Passport (user ↔ agent binding)
- Schema pin & optional plan contract validation
- PDP decision → constraints & obligations
- PEP enforcement (budgets, egress, params)
- Tool call
- Receipt emission and chain update
- Analytics verify and update budgets
Watch the overview
Prefer video? Watch a 2‑minute ARIA overview.